Introduction
In today’s tech-powered world, it’s easy to come across strange-looking alphanumeric strings like 001-gdl1ghbstssxzv3os4rfaa-3687053746. At first glance, it might seem like a jumbled mess of characters. But there’s more to it than meets the eye.
These types of unique identifiers (UIDs) are essential behind-the-scenes players in how websites, apps, databases, and digital systems stay organised, secure, and scalable. Whether you’re in web development, digital marketing, data science, or just curious about how systems work, this guide will give you a clear, easy-to-understand look into the importance of these codes and how they function.
What Is 001-gdl1ghbstssxzv3os4rfaa-3687053746?
This string is a Unique Identifier (UID). It’s a label designed to help distinguish one piece of data from another—whether that’s a user, transaction, session, product, or log entry. These identifiers are used across countless digital environments:
- In databases, to prevent data overlap
- In APIs to manage sessions and user access
- In digital marketing, to track user behaviour
- In software to debug and trace actions
- In e-commerce for inventory and order management
If you think of every digital element needing its own name tag, this is exactly that.
Breaking Down the Structure

When looking at 001-gdl1ghbstssxzv3os4rfaa-3687053746, the format tells us something important. The string is divided into three segments separated by hyphens, which is a common pattern in identifier design.
The first segment “001” could represent a prefix indicating a category, region, or version. The middle portion “gdl1ghbstssxzv3os4rfaa” appears to be a randomly generated alphanumeric code that ensures uniqueness. The final segment “3687053746” might be a timestamp, sequential counter, or numerical hash that adds another layer of distinction.
This structured approach helps systems process and categorise information efficiently while maintaining the core purpose of uniqueness.
Why Unique Identifiers Matter
Unique identifiers serve as the backbone of modern digital infrastructure. Without them, systems would struggle to differentiate between millions of users, transactions, or data entries. Imagine an e-commerce platform trying to manage thousands of orders without a way to tell them apart—chaos would ensue.
These codes enable seamless database operations, allowing developers to query specific records instantly. They facilitate API communication by providing secure tokens for authentication. They support analytics platforms in tracking user journeys across multiple touchpoints. The reliability of digital services depends heavily on the proper implementation of these identification systems.
Common Use Cases in Technology
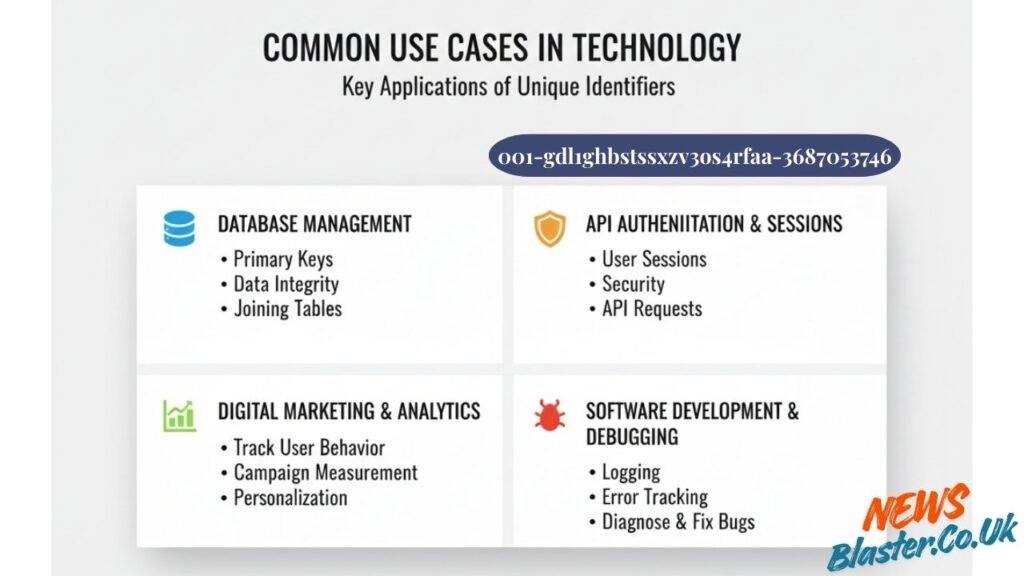
Database Management
In relational and non-relational databases, unique identifiers like 001-gdl1ghbstssxzv3os4rfaa-3687053746 serve as primary keys. They ensure that each row or document can be accessed without ambiguity. When joining tables or establishing relationships between data sets, these identifiers become the connecting threads that maintain data integrity.
API Authentication and Sessions
Web applications use UIDs to manage user sessions and API requests. When someone logs into a website, the system generates a session identifier that tracks their activity. This prevents security vulnerabilities and ensures that actions are attributed to the correct user account.
Digital Marketing and Analytics
Marketing platforms rely on unique identifiers to follow user behaviour across websites and campaigns. These codes help marketers understand conversion paths, measure campaign effectiveness, and personalise user experiences. Privacy regulations have made this more complex, but the fundamental need for tracking mechanisms remains.
Software Development and Debugging
Developers use UIDs extensively for logging and error tracking. When an application encounters an issue, the unique identifier associated with that event makes it possible to trace the problem back through system logs, helping teams diagnose and fix bugs more efficiently.
How These Identifiers Are Generated
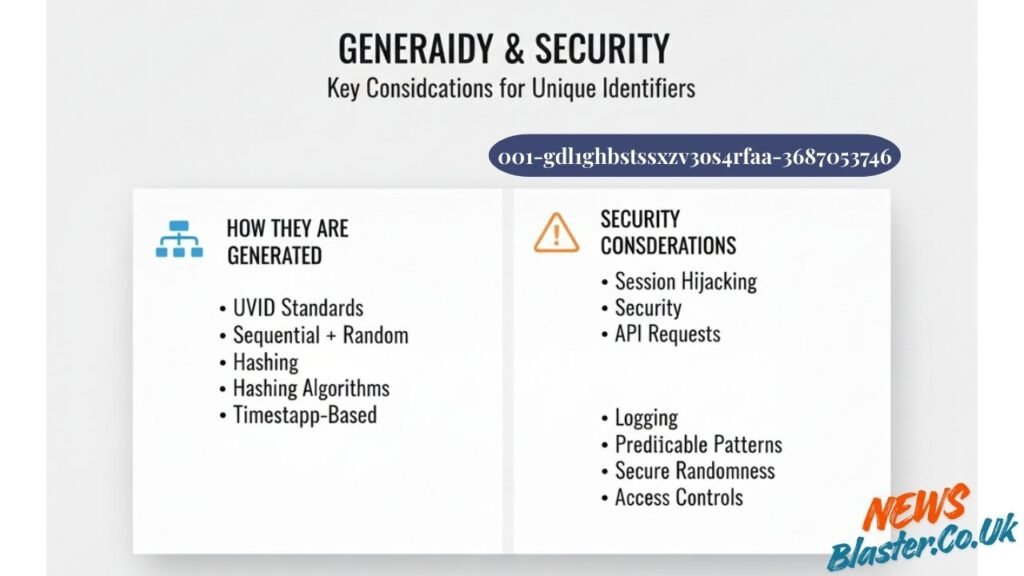
The creation of unique identifiers involves various methods depending on the system requirements. Some platforms use UUID (Universally Unique Identifier) standards, which generate codes with extremely low collision probability. Others employ sequential numbering combined with random elements.
Hashing algorithms can transform input data into fixed-length strings that serve as identifiers. Timestamp-based generation adds temporal context to the code. The choice of method depends on factors like scalability needs, security requirements, and system architecture.
Security Considerations
While unique identifiers are not typically sensitive data themselves, they can become security vulnerabilities if mishandled. Exposing session identifiers in URLs can lead to session hijacking. Predictable patterns in UID generation might allow attackers to guess valid identifiers and access unauthorised resources.
Best practices include using cryptographically secure random generation, implementing proper access controls, rotating identifiers regularly, and avoiding the exposure of sensitive UIDs in client-facing code or URLs. Systems should treat these codes with appropriate care to maintain the overall security posture.
Performance and Scalability
As systems grow, the efficiency of unique identifier generation and lookup becomes critical. Database indexes built on these codes must remain performant even with billions of records. The length and format of identifiers affect storage requirements and query speed.
Distributed systems face additional challenges in ensuring uniqueness across multiple servers or data centres. Solutions like Twitter’s Snowflake algorithm and MongoDB’s ObjectId address these concerns by incorporating server identifiers and timestamps into the generation process.
Best Practices for Implementation
When implementing unique identifier systems, developers should consider several key principles. Choose formats that balance uniqueness with practical constraints like storage size. Document the structure and generation logic for future maintainability. Implement proper indexing strategies to ensure fast lookups.
Avoid reusing identifiers even after deletion of associated records, as this can lead to confusion and potential data integrity issues. Plan for migration paths if identifier formats need to change. Test the generation mechanism under load to ensure it can handle production scale.
The Future of Unique Identifiers
As technology evolves, so do the requirements for identification systems. Blockchain technology introduces decentralised approaches to unique identification. Privacy-enhancing technologies seek ways to provide functionality without compromising user anonymity. Machine learning systems generate new demands for tracking model versions and data lineage.
The fundamental concept of uniquely identifying digital entities will remain central to technology infrastructure, even as the specific implementations continue to adapt to new challenges and requirements.
Conclusion
The string 001-gdl1ghbstssxzv3os4rfaa-3687053746 represents far more than a random collection of characters. It embodies the systematic approach modern technology takes to organise, secure, and scale digital operations. Understanding these unique identifiers provides insight into how websites remember your preferences, how databases maintain accuracy, and how systems stay coordinated across the digital ecosystem.
Whether you’re building applications, analysing data, or simply appreciating the complexity behind everyday digital interactions, recognising the role of these identifiers helps demystify the technology that powers our connected world.
Also Read: Logisths Transforming Modern Supply Chain Management

